SharkTrust™ revolutionizes how you handle security (PKI) for your internal web servers. Whether you have a product with an Embedded Web Server or any other type of server, SharkTrust can help you automate and streamline the PKI process. And the best part? SharkTrust is free to use, with the source code available on GitHub for your convenience. Trust SharkTrust to keep your PKI organized and your business moving forward.
Understanding certificate management and PKI can be complex and challenging. If you struggle with these concepts or need more clarity on SharkTrust, explore our tutorial on Certificate Management and Chain of Trust. This detailed guide will introduce you to the essential aspects of certificate management and help you understand the PKI concept.
With SharkTrust™, you can provide your users with a seamless and secure experience when using your product on a private network. Setting up SSL Certificates can be a technical and time-consuming process, but SharkTrust completely automates it, making it easy for even those without PKI knowledge to access all their devices securely. This enhances the user experience and frees your support team to focus on other important tasks. Don't let complicated PKI processes hold your product and business back - implement SharkTrust™ and see the benefits for yourself.
Is the following what your customers see when they first start using your embedded web interface?
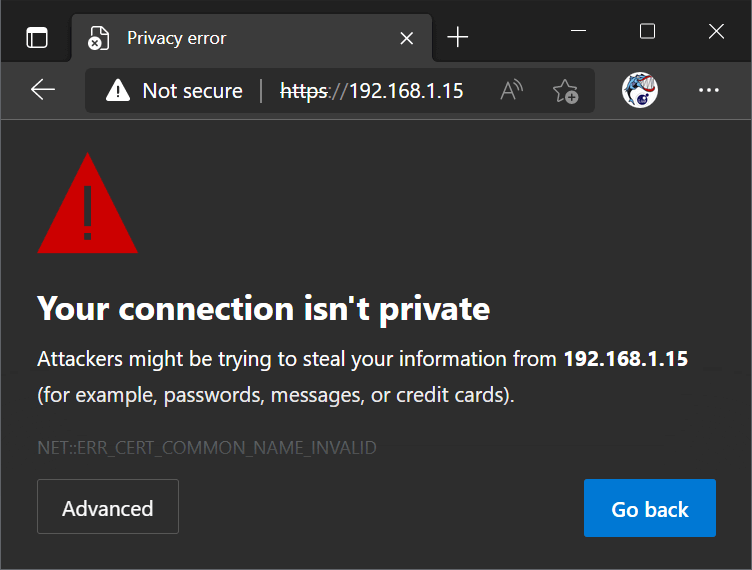
The user cannot differentiate between a man in the middle and the nontrusted server's certificate when the user is forced to bypass the browser's security warning. See the tutorial hack any web server-enabled product for more information.
As a device manufacturer, it's important to ensure that your customers can securely communicate with your product(s) through any web browser. While some manufacturers opt for a nonsecure HTTP connection, this has several disadvantages. Many companies now mandate security on private networks, especially when sensitive information is involved. Failing to provide HTTPS may discourage them from using your product. Additionally, many modern browsers are now flagging all HTTP connections as insecure, which can be off-putting for users and may even prevent certain browser features, like password managers, from functioning properly. This can negatively impact the user experience of your product. That's why many manufacturers are now turning to HTTPS to ensure secure communication and a positive user experience.
Using a self-signed SSL certificate may seem like a simple solution for secure communication with your product, but it comes with its own set of challenges. Browsers do not trust these certificates, leading to a warning message for users about an insecure connection. While it is possible to bypass this warning, it effectively turns the connection into a non-trusted HTTP one, which can limit certain browser features that rely on HTTPS. This can hurt the user experience when communicating with their devices. It's important to consider these factors when choosing an SSL certificate for your product to ensure a positive user experience.
Purchasing a certificate from a Certificate Authority (CA) allows your users to have a secure HTTPS connection when communicating with their devices. However, CAs do not issue certificates for private networks, and this means your users must implement a Public Key Infrastructure (PKI) solution to get one. Existing PKI solutions typically require that users go through a lengthy, technically challenging setup process, making using your product securely much more difficult. PKI tutorials are typically targeted at engineers, and your users may find them challenging to understand and follow. Additionally, you may find yourself spending valuable resources supporting customers with this process, causing headaches both for you and your customers.
Apple’s Safari browser now limits certificate validity to one year and the other browser vendors will soon follow. The question is "Where do things go from here?" Since long-lived certificates are a security risk, browser vendors will move to even shorter renewal periods. Eventually, all browsers will refuse certificates with expiration dates longer than three months, and manually updated certificates will eventually be too time-consuming and impractical.
With SharkTrust, you do not have to worry about ensuring safe and secure communication with your product from any browser, nor do your users. By connecting to an online web interface, users can access information about all the devices on their network, and connecting to a device securely is as simple as clicking on it.
SharkTrust™ works with any embedded web server and TLS product, enabling you to integrate our automatic DNS and certificate management solution as a go-to option for customers requiring a configuration-less PKI solution for their private network.
SharkTrust's root certificate (CA certificate) is directly trusted by all major browsers and operating systems, including Microsoft, Google, Apple, Mozilla, Oracle, and Blackberry. This means that no matter what device or browser is being used to connect with your product's Embedded Web Server, your users will never experience uncomfortable warning screens about unsecured connections.
SharkTrust uses the automated Let's Encrypt Certificate Authority and the Automatic Certificate Management Environment (ACME) protocol specified in RFC-8555.
The device simply needs to conform to the easy to implement SharkTrust Binary Protocol. SharkTrust may be used by any microcontroller-based solution using any embedded TLS stack as long as the embedded TLS stack can load a standard X.509 certificate and the associated private key.
SharkTrustX comes pre-integrated as a ready to use Barracuda App Server plugin. Unlike SharkTrust, SharkTrustX communicates directly with Let's Encrypt using the ACME protocol (RFC-855). The plugin also manages private key generation, certificate signing requests, and required cryptology. An online service is still required but is limited to managing the DNS.
SharkTrust and SharkTrustX require internet access to automatically update certificates approximately once every 2 to 3 months for each device. However, before excluding SharkTrust as an option simply because your customers do not have internet, consider the complexity of setting up a Public Key Infrastructure (PKI). Setting up a PKI is far from straightforward. For the average user or even businesses without dedicated IT specialists, this process can be daunting:
Given these challenges, it's clear that setting up and managing a PKI is not feasible for most unless they have dedicated PKI experts on their payroll.
Your customers may not be connected to the Internet for the two following reasons:
Both issues can easily be remedied with modern equipment:
Why SharkTrust is the Optimal Solution: Against the backdrop of these challenges, SharkTrust offers a seamless, worry-free alternative:
In light of these considerations, SharkTrust isn't just a good option; for many businesses, it's the only viable option to maintain rigorous security standards without needing specialized expertise.
Looking for a straightforward way to test SharkTrustX on a microcontroller? Here's how:
Don't have an ESP32 but are eager to set up an Intranet Web Server with a trusted certificate? No worries! The following video tutorial guides you through compiling the same software for Linux. It's quick and easy, and you will be done in 5 minutes.
SharkTrust and SharkTrustX are powerful tools licensed under the open-source MIT License, meaning they can be used free of charge. They can greatly enhance your products' security, but setting up your own portal requires some expertise. That's where Real Time Logic comes in - we're here to provide the initial consultation and support you need to get your SharkTrust or SharkTrustX portal instance up and running smoothly. Contact us to schedule your consultation and get started with SharkTrust today!