|
INTRODUCTION IoT protocols may sometimes add unnecessary memory and processing overhead. The below demonstrations illustrate how one can design a secure IoT Edge Node merely by using a TCP/IP stack in combination with SSL where the payload data is exchanged between a server and the device using an encrypted connection. |
Each demonstration program initiates a connection that allows for ease of penetration and transfers through firewalls and proxies. A secure encrypted TCP/IP connection is established for data exchange after connection to the server.
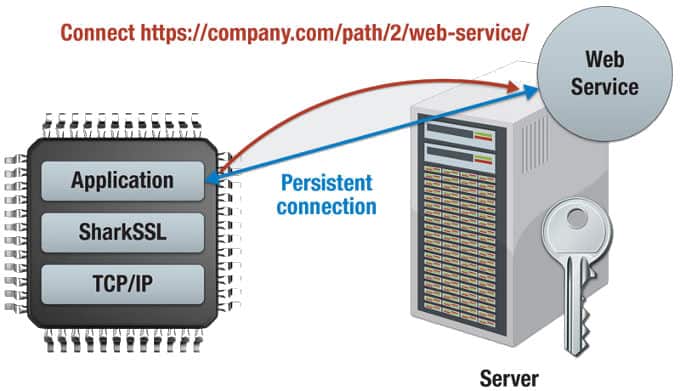
Figure 1: Device connects to a Web Service by sending an initial HTTP header that is then morphed into a persistent socket connection upon connection with the server. Data sent over the persistent connection is then encrypted by the SSL stack.

M2M-LED Demo