Authentication
The Barracuda Application Server (BAS) offers a robust and flexible authentication framework. It seamlessly integrates with the Virtual File System (VFS) to provide secure access control across web applications. Understanding how authentication interfaces with the VFS is crucial for implementing effective security measures.
Authentication Overview:
Authentication verifies a user's identity by comparing provided credentials (username and password) against stored credentials on the device or via methods such as single sign-on.
Decoupled Authentication Logic:
BAS decouples authentication logic from web pages by associating authenticators with VFS directory nodes. This design allows an authenticator to act as a security umbrella, enforcing authentication for all resources within a specific directory and its subdirectories. By attaching an authenticator to a directory node, you ensure that any access to resources within that node requires proper authentication, streamlining security management and reducing the risk of unauthorized access.
Understanding Session Management and Authentication in BAS
When a user is authenticated using one of the built-in BAS authenticators, the system automatically creates a session object. This session keeps track of the authenticated user and is maintained either through a session HTTP cookie or a session ID embedded in the URL. To strengthen security, both methods lock the session to the client's IP address, which helps prevent session hijacking. However, if your use case does not require session tracking or if you need more flexibility, such as allowing roaming IP addresses, you can create your own authentication mechanism. By implementing a custom directory function, you can enforce your own access control while still providing the same security umbrella as the built-in system. Any files or APIs inside the protected directory, including its subdirectories, will then be secured by your custom logic.
Supported Authentication Methods
Introduction
BAS supports standard Basic, Digest, and form-based authentication, as well as custom authentication such as bearer tokens. The server also provides straightforward integration with user/password databases.
The Barracuda Server supports the following authenticator types:
- Basic: Implements Basic authentication as specified in RFC-2617.
- Digest: Implements Digest authentication as specified in RFC-2617.
- Form: Form-based authentication is modeled after the J2EE server specification. You provide a login form and an error page. The authenticator takes care of the rest.
- Default: The default authenticator implements all authenticators, basic, digest, and form. The client chooses the method of authentication.
- Dav: The WebDAV authenticator implements basic and digest authentication. This authenticator also includes code for accepting the non-standard authentication headers sent by Microsoft clients.
- Custom: The server also supports custom authentication methods, such as Single Sign-On (SSO) and WebAuthn.
Details
- HTTP-Based Authentication Methods:
- Basic Authentication: Transmits credentials in clear text (base64-encoded), making it suitable only when combined with SSL/TLS to ensure security.
- Digest Authentication: Encrypts credentials before transmission, offering enhanced security over Basic Authentication.
Both methods involve the server challenging the client with a 401 Unauthorized response, prompting the client to provide valid credentials. However, these methods can present challenges, such as difficulty implementing custom login interfaces and managing user logout processes, especially with browser-controlled authentication dialogs.
- Form-Based Authentication:
To overcome the limitations of HTTP-based methods, BAS supports form-based authentication, which is particularly advantageous for browser clients:
- Customizable Login Interfaces: Allows the creation of user-friendly login pages that align with the application's design.
- Simplified Logout Processes: Enables easier management of user sessions and logout procedures, as authentication is handled within the application rather than the browser.
In form-based authentication, user credentials are submitted through an HTML form. It's important to note that these credentials are transmitted in cleartext unless protected by SSL/TLS, posing potential security risks.
- Passwordless Authentication
BAS supports modern passwordless authentication methods, enhancing security and user experience:
- Single Sign-On (SSO):
- Integrates with external identity providers, allowing users to log in once and access multiple services without re-entering credentials.
- This can be implemented using OAuth with a ready-to-use library for Microsoft Entra Single Sign-On.
- WebAuthn (Web Authentication):
- Uses cryptographic key pairs instead of passwords.
- Supports biometric authentication (fingerprint, face recognition) and hardware security keys (FIDO2 devices).
- Eliminates password phishing risks and improves security.
Integrating Authentication with the VFS
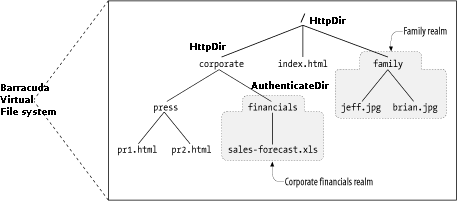
In BAS, the VFS allows for the hierarchical organization of resources, with each directory node capable of having its own authenticator. This structure enables the implementation of distinct security realms within the application. For instance, a directory node handling sensitive data can be assigned a strict authenticator, while another node may permit public access.
By leveraging the VFS, you can define specific authentication and authorization policies for different sections of your application, ensuring that users have appropriate access based on their credentials and roles.
Authorization and User Roles
Beyond authentication, BAS provides mechanisms for user authorization, determining whether an authenticated user has permission to access or perform actions on specific resources. This is typically managed through the implementation of an authorizer, which evaluates user permissions based on factors such as URL paths and HTTP methods.
Implementing role-based access control (RBAC) allows for more granular authorization, where users are assigned roles that define their permissions within the application. This approach enhances security by ensuring users can only access resources and perform actions pertinent to their roles.
Tracking Logins
A login tracker can be associated with an authenticator as an optional security enhancement. A login tracker keeps track of failed and successful logins and their IP addresses.
A login tracker prevents dictionary and brute-force attacks. A dictionary attack consists of trying "every word in the dictionary" as a possible username-password combination. A weak password may be easily cracked if the authenticator does not keep track of failed logins. This is where the login tracker comes to the rescue. The login tracker keeps a configurable-size RAM database of users attempting to log in. A user can be banned if too many login attempts are made.
A login tracker can be associated with an authenticator created by Lua code, but the actual login tracker code must be initialized by the C/C++ startup code. A C/C++ developer can either create a customized login tracker by using the provided login tracker APIs, or use the default login tracker. The default login tracker adds Lua bindings for fetching login tracker information.
Lua and C/C++ Documentation
Lua Authentication and Authorization Tutorials
- Authentication Examples (collection)
- This tutorial provides an introduction to Basic, Digest, and form-based authentication. It demonstrates how to manage user sessions, handle login and logout functionality, and protect restricted areas of a web application.
- The example showcases a session-based authentication system, where users log in with credentials, and session cookies are used to maintain authentication across requests.
- GitHub Repository
- Authentication and Authorization Example
- Dynamic Navigation Menu
- This tutorial demonstrates how to create a fully functional navigation menu using server-side code. It includes ready-to-run source code examples for building dynamic menus.
- The example source code incorporates a seeded hash-based form authenticator, enhancing security by ensuring that authentication remains secure even on non-TLS connections.
- GitHub Repository
- Dashboard Application
- This tutorial provides a ready-to-use foundation for building industrial web applications. It demonstrates how to create a web-based management interface by leveraging a directory function to dynamically map URLs to files.
- The example includes user authentication mechanisms to restrict access to certain parts of the dashboard, and includes a soft TPM-protected (encrypted) user database, along with a web interface for adding and removing users. The authentication logic is based on the example provided with function ba.tpm.jsonuser().
- GitHub Repository
- Single Sign-On (SSO)
- This tutorial addresses security vulnerabilities associated with pre-installed passwords by implementing Single Sign-On (SSO) solutions.
- The example demonstrates how to configure SSO, allowing users to authenticate through a centralized identity provider, thereby mitigating risks associated with static passwords.
- GitHub Repository
- Passwordless Authentication with WebAuthn
- This tutorial demonstrates how to implement WebAuthn-based authentication, and introduces passwordless login, eliminating traditional credentials in favor of FIDO2-compliant authentication.
- The example provides a fully functional WebAuthn authentication flow, including user registration, authentication, and session management. It supports public-key cryptography, biometric authentication, and security keys, ensuring high security without passwords.
- WebAuthn for Embedded Web Servers, an introduction
- GitHub Repository
- RADIUS Authentication
- This tutorial shows how to delegate user authentication to an external RADIUS server from within a web application. By integrating a Lua-implemented RADIUS client with the server's authentication system, you can centralize credential validation.
- GitHub Repository
- OAuth 2.0 Authentication Example
- This tutorial provides an example of implementing OAuth 2.0 authentication to access GitHub's API. It covers the process of obtaining authorization from users and accessing protected resources.
- The example showcases how to integrate third-party authentication by guiding users through the OAuth 2.0 flow, including obtaining access tokens and making authenticated API requests.
- GitHub Repository
